
This post was originally written in 2020, but we’ve updated it to be more accurate in 2021.
If you prefer, you can listen to a podcast episode on this topic at Constant Variables or by pressing play below.
Like any good software developer, hackers are lazy.
When you picture a hacker, you’re likely thinking of a guy in front of a computer screen, furiously typing away on his keyboard as the characters fly by on the screen.
In reality, a nefarious individual is going to look for the easiest way into your system. The easiest way isn’t to try and break the encryption on your database or type in every combination of characters to guess your passwords.
Often, the easiest way is to trick you into giving them the keys.
Enter Social Engineering.
Social engineering is a catch-all phrase used by security professionals to describe the various ways criminals trick you into giving them access to your system or confidential information.
Social engineering attacks are behind some of the most infamous breaches of recent times, including the 2016 Democractic Party email leak, the 2013 Target breach, and the 2011 RSA hack, of which the full story was just recently told.
In this post, we will talk about the most common types of social engineering attacks and what you can do as a business to help prevent them.
What makes Social Engineering so effective?
Social engineering works because humans are prone to relying on their cognitive biases when making decisions.
For example: a bad actor walks into a business and puts up a sign with an updated help desk number. The next time someone needs help with their computer, they call the hacker who asks them for their login information. Because the number was posted in the building and it looked official, why would the employee question it?
Robert Cialdini, a psychology and marketing professor, developed a theory that says influence over others is based on these six key principles:
- Reciprocity: People tend to return a favor.
- Commitment and consistency: If people commit to an idea or goal, they are more likely to honor that commitment even if the original incentive is removed after they agreed.
- Social proof: People will do things that they see another person doing.
- Authority: People tend to obey authority figures even if they are asked to perform objectionable acts.
- Liking: People are easily persuaded by people they like.
- Scarcity: Perceived scarcity generates demand.
Social engineering is when bad actors exploit these biases by combining several of them to trick you into giving them the information they need.
What are examples of common Social Engineering attacks?
Phishing
I would venture to guess that most users of the internet are familiar with the term “phishing”.
Phishing is when an attacker tries to get you to divulge personal information while disguised as a trustworthy source.
One of the most common phishing attacks is when your “bank” sends you an email that says you had a thousand dollar charge to your credit card and asks you to sign in to verify the transaction.
Clicking a link in that email brings you to a website that looks like your bank’s site, but on the other end, the attacker is saving your username and password to use on your real bank’s site.
Phishing attacks are generally broad in scope, meaning an attacker sends out a million emails to random people with the hopes of getting one or two victims.
Spear phishing
When an attacker crafts their message for a specific person or organization, this is known as “spear phishing”.
The Podesta email hack during the 2016 presidential election is a perfect example of a spear phishing attack. The Fancy Bear cyber espionage group crafted a Google security warning that led to a custom Gmail sign in page.
Vishing
A subset of phishing, vishing (“voice phishing”) is when an attacker uses social engineering over the phone to gain access into a system or learn more about a particular target.
Back in 2012, a reporter named Mat Honan was the victim of an attack which involved vishing. If you haven’t heard of his story, take a few minutes and read it. It’s insane.
Watering hole
A watering hole attack targets victims in a particular group. They figure out which websites are used most frequently by members of the group and infect one of those sites with malware. Eventually, someone downloads a file from the infected website.
Let’s say you are looking to hack a movie studio. You might do some research and see that they frequently need to download drivers to connect their cameras to their computers. You could create a fake site that hosts drivers for all different kinds of cameras.
Then, you would wait for someone to discover your site and download a driver. Attached to the driver is a piece of malware that would monitor the system and help you find a way in.
Baiting
A baiting attack promises some sort of reward to the victim to get them to launch a file.
As an example, let’s say you are looking online for a movie that is not yet released. You might download a file and open it, expecting to watch that movie, but instead, it’s some form of malware.
A business-case example of baiting is more of a real world attack: malware-infected flash drives. An attacker might drop some flash drives in the parking lot near your work, hoping that you’ll plug it in to see what’s on there. When you plug it in, it automatically installs the malware and infects your system.
Pretexting
Pretexting is when an attacker invents a scenario to convince victims to give up information that they normally would not divulge.
In the enterprise world, an attacker would use pretexting to call the support line over the phone and impersonate their victim, hoping that they can convince you to divulge information.
Another common pretexting attack is when an attacker tries to trick a low level employee into transferring large amounts of money into offshore accounts. For example, an attacker could figure out who is a newer accounting person and give them a call pretending to be a C-level executive. They would claim that they need an emergency transfer of funds to another account and that they are giving the authorization.
If your organization maintains customer information, you need to be aware of pretexting and train your employees to not give exceptions to the established procedures, no matter how convincing a “customer” sounds.
Quid pro quo
Quid pro quo is Latin for “something for something”.
An example of a quid pro quo attack would be an attacker who gets a hold of a list of phone numbers for a company. They would call each number and claim they were tech support returning their call.
Most people would say they never reached out to the help desk, but eventually, they’ll find someone who did reach out and has a legitimate problem. Because they are so thankful that they returned their call, they are willing to type in any commands that the help desk gives them to “fix” their problem.
Tailgating
Tailgating is when an attacker follows an authorized person into a restricted area.
Let’s say you work for a company who has keycard access into the building. As you swipe your entry in, another person comes up behind you at the same time. Common courtesy would dictate that you hold the door open for them, and now they’re in the building.
How can I prevent my business from falling for social engineering attacks?
Humans will be humans. That is why social engineering works so well. We can’t help but hold the door open for the guy carrying a bunch of stuff behind us or check out what’s on the flash drive we found in the hallway.
It’s very hard for us to break our cultural conditioning and our cognitive biases, so it all comes down to end user education.
Here are some tactics you can implement to ensure you stand the best chance of protecting yourself from yourself (and from your employees accidentally making a mistake):
Get your processes in place (and don’t deviate from them)
Any good business will have their processes for handling tasks. This ranges from customer service scripts to accounting payments.
Make sure your team buys into these processes and that they don’t make exceptions. If (and when) they are faced with a situation that isn’t covered by a process, train your team to slow down and ask for assistance from a supervisor.
Explain why your processes are in place
People can’t stand processes, especially when they slow you down from taking care of your customer.
I’ve found that when I’m told exactly why a process exists and how it helps save me from making a mistake, I’m more likely to follow it.
Treat your employees like humans and help them become aware of their cognitive biases.
Train your team
This ties into the last point, but your team needs to be made aware of their processes.
According to the 2020 State of the Phish report, 95% of organizations train employees how to identify and avoid social engineering attacks.
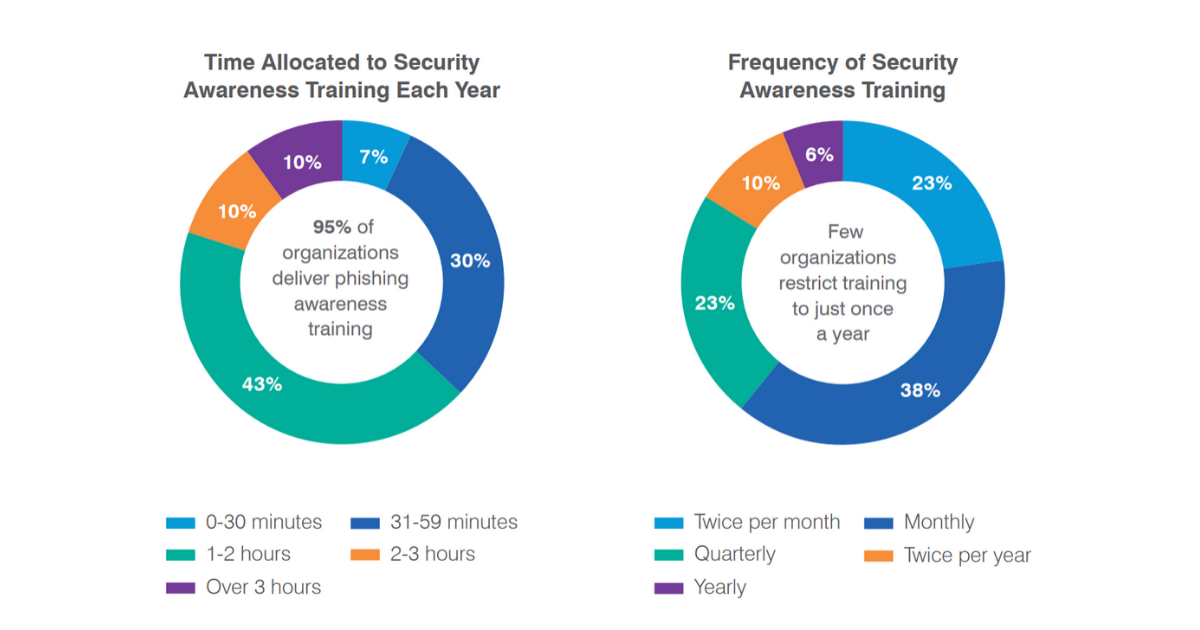
Take some time and think through some possible social engineering attacks that could affect your organization. Present those scenarios to your team and have them act out what they would do in those situations.
The better you train your team, the less likely they are to fall for a scam.
Frequently test your team
Nothing is more effective at teaching someone a lesson than failure.
Wouldn’t you rather have your customer support team get hacked by someone you are paying to find vulnerabilities?
There are companies you can hire to test your team and make sure they are following the proper procedures when faced with a possible social engineering attack.
Stay up to date on the latest social engineering attacks
You don’t need to become a security expert, but pay attention to the news. If you see an article about an organization who was hacked, read it and find out how that organization was hacked.
Once you hear of a new social engineering attack, try it out on your team. Work together to figure out how your team would defend against it, and put a procedure in place to safeguard yourself against that attack.
Social engineering attacks can be hard to spot. The best advice for preventing an attack on your organization is to stay vigilant by introducing the concept of social engineering into your company’s culture.
 Tim Bornholdt
Tim Bornholdt

